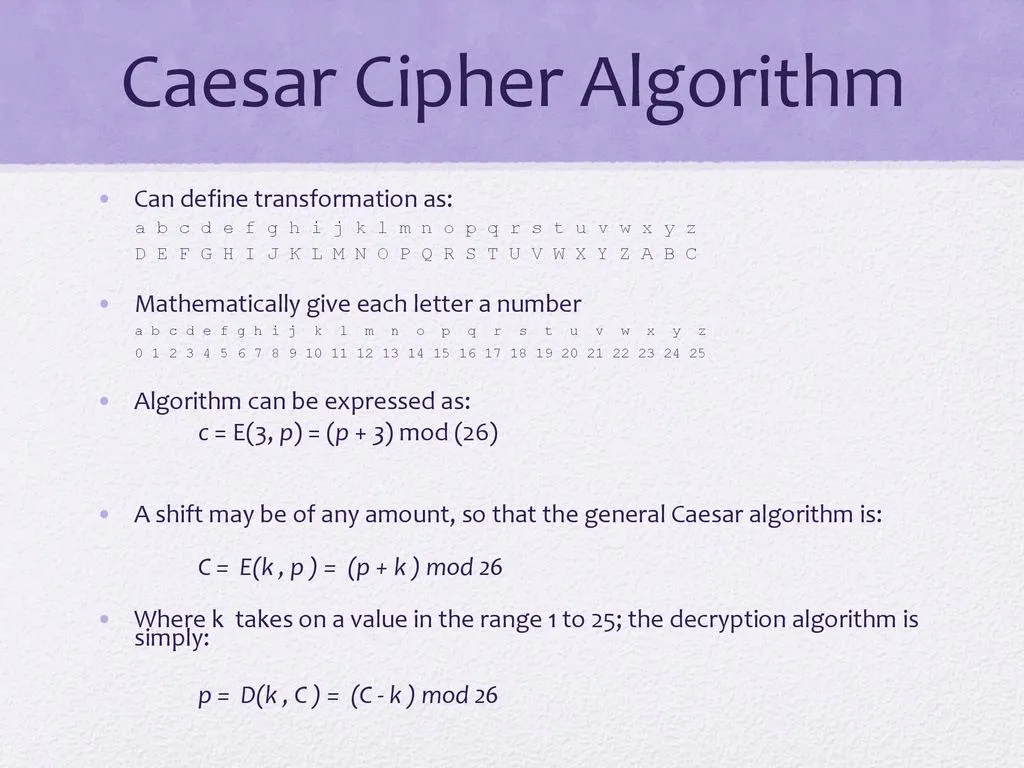
The Caesar Cipher is one of the oldest and simplest encryption techniques used in cryptography. It is a substitution cipher, where each letter in the plaintext is replaced by a letter a certain number of positions down the alphabet. While the Caesar Cipher is easy to understand and implement, it is also very easy to crack, making it unsuitable for secure communication.
Limitations of the Caesar Cipher
The Caesar Cipher has several limitations that make it vulnerable to attacks. One of the main limitations is the small key space, which consists of only 25 possible keys. This makes it easy for an attacker to use brute force attacks to try all possible keys until they find the correct one. Additionally, the Caesar Cipher is vulnerable to frequency analysis attacks, where an attacker can use the frequency of letters in the ciphertext to deduce the shift used in the cipher.
Overcoming the Security Challenges of the Caesar Cipher
There are several ways to overcome the security challenges of the Caesar Cipher. One way is to use a larger key space, which makes it much harder for an attacker to use brute force attacks. Another way is to use a variable key, where the shift value is randomly generated for each message. This makes it much harder for an attacker to crack the cipher, as they would need to try all possible keys for each message.
Another way to overcome the security challenges of the Caesar Cipher is to use a more complex encryption technique. For example, the Vigenere Cipher is a polyalphabetic substitution cipher that uses a series of different Caesar Ciphers based on a keyword. This makes it much harder to crack than the Caesar Cipher.
Applications of the Caesar Cipher in Modern Times
Despite its limitations, the Caesar Cipher is still used in various applications today. For example, it can be used to create simple puzzles or to hide spoilers in online forums. It is also used in computer science education to teach the basics of cryptography. Additionally, the Caesar Cipher is sometimes used as a building block in more complex encryption algorithms.
In conclusion, while the Caesar Cipher is an important historical encryption technique, it is not suitable for secure communication due to its vulnerabilities. However, there are several ways to overcome the security challenges of the Caesar Cipher, such as using a larger key space, a variable key, or a more complex encryption technique like the Vigenere Cipher. Despite its limitations, the Caesar Cipher remains relevant in various applications today.
